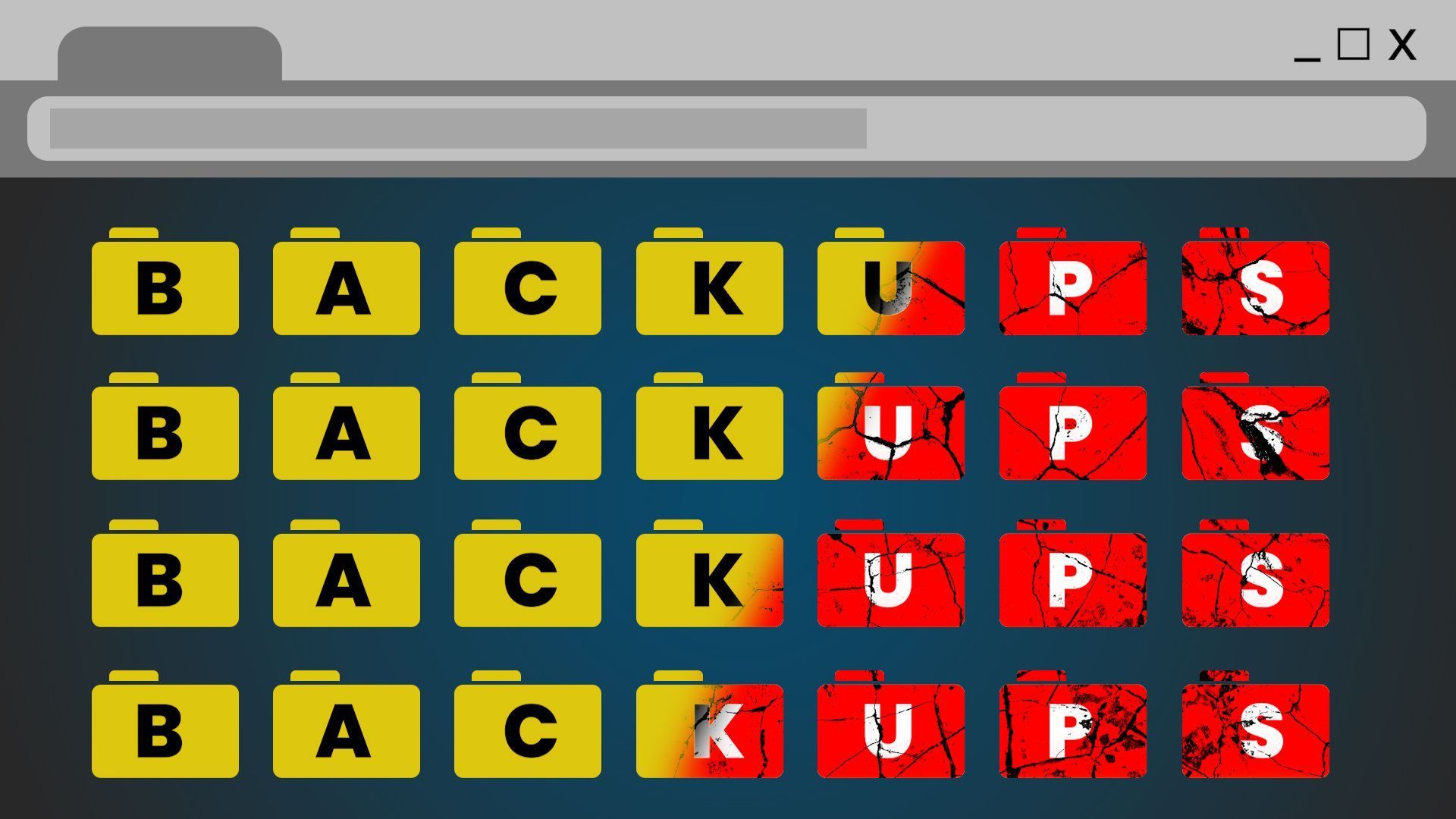
Weak passwords are still one of the biggest risks to your business – and attackers know it.
From “123456” to reused logins, poor password practices make it easy for cyber criminals to get in and cause serious damage. In this blog, we break down why passwords aren’t enough anymore, what better options look like, and how your business can upgrade its login security for good.

Think your Microsoft account is safe behind a strong password and MFA? Think again.
A new tactic called device code phishing is letting cyber criminals bypass traditional security – using real Microsoft login pages to trick users into handing over access. In this blog, we break down how the attack works, why it's so dangerous, and what your business can do to stay ahead of it.

Think your team would never fall for a phishing scam? Think again.
86% of employees say they’re confident in spotting scam emails—but over half have already fallen for one. This blog explores how overconfidence is a hidden cybersecurity threat, and what you can do to protect your business before it's too late.

If you use Microsoft 365 Business Standard, you’ll already know about the range of tools and features that help your business function better every day.
But what if there was an alternative? One that offered all the same tools and features AND improved protection from the security threats and risks your business faces?
That’s what Business Premium does. Take a look...

Microsoft recently announced that all Azure sign-ins will soon require multi-factor authentication (MFA) to boost security. Even if you don’t use Azure, a cloud computing platform, this is something you should pay attention to. Because MFA is one of the simplest and most effective ways to protect your digital assets.

If you’re like most people, you probably find system updates a hassle. They take ages and those big downloads eat up precious bandwidth and storage.
Good news then: Microsoft is about to make your life a whole lot easier with the upcoming Windows 11 24H2 update.
It’s introducing something called ‘checkpoint cumulative updates.’ That might sound a bit technical, but don’t worry – it’s simple and very beneficial. Find out more in our blog post...

Buying a used laptop can be a great way to save money. But it comes with risks. You need to be careful and thorough in your evaluation. Otherwise, you could end up wasting your money.
You can’t only look at the outside when evaluating technology. This guide will help you understand what to look for when buying a used laptop (or desktop PC). These steps can keep you from losing money on a bad tech decision.

Running a small business is a whirlwind. You juggle a million tasks and wear countless hats. You also constantly fight the clock. What if you could reclaim some of that precious time?
Enter task automation. It’s your secret weapon for streamlining your workflow and boosting productivity. By automating routine and repetitive tasks, small businesses can gain many benefits. Such as freeing up valuable time and resources. Every minute saved can translate to increased productivity and profitability.
This guide will walk you through the essentials of small business task automation. It’s designed to help you understand its benefits and identify tasks to automate. As well as choose the right tools and install automation effectively

Imagine this: you walk into your office on a busy Monday morning, ready to tackle the week. But something's wrong. Computers are unresponsive. Phones are silent. The internet is a ghost town. Your business has come to a grinding halt – victim of an IT outage.
It's a scenario every business owner fears. But beyond the initial frustration are expenses you may not immediately see. IT downtime carries hidden costs that can significantly impact your bottom line. Let's peel back the layers and expose the true price of IT outages.